Signed in as:
filler@godaddy.com
Signed in as:
filler@godaddy.com
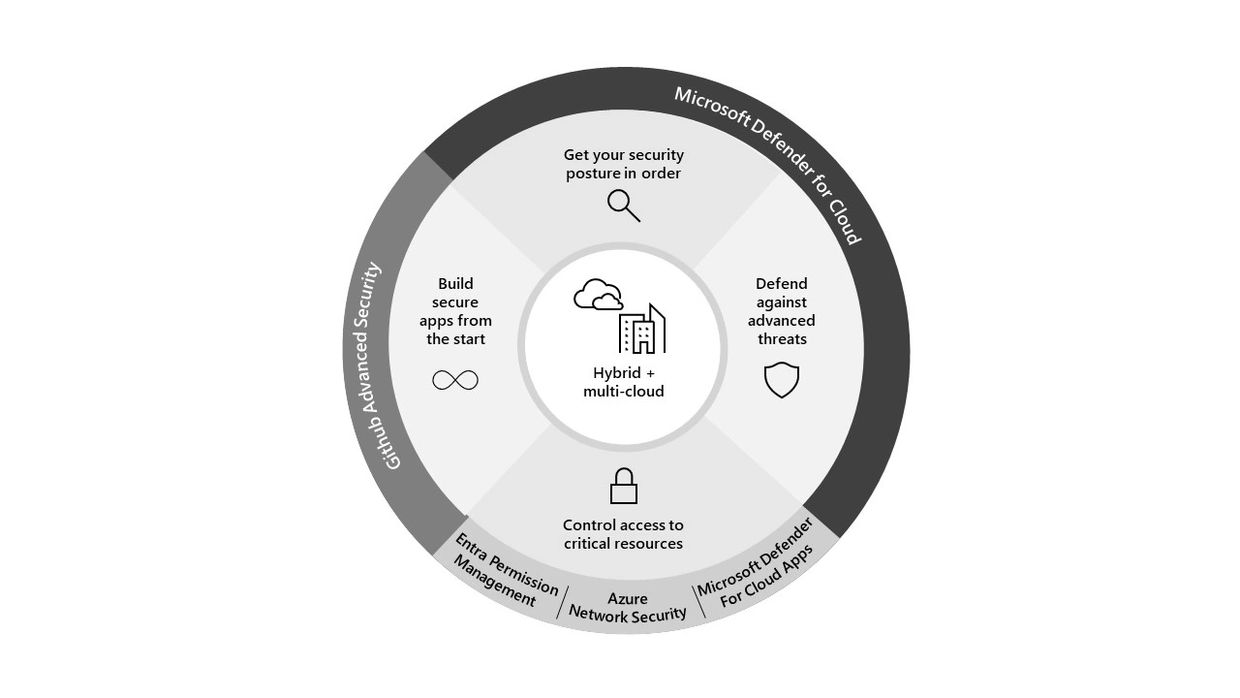
We’re in an era of transformation—digital, cloud, and security—and organizations are navigating it in unique ways. Accelerated in large part by the migration of workloads and apps to the cloud, work patterns and business operations have been reshaped or completely reimagined. For example, 91% of IT decisionmakers indicated that their organization uses at least two different public clouds. To stay ahead of potential threats, enterprises must modernize their approach to protecting their expanding landscape of cloud resources.

Easily assess and improve the secure configuration of your critical multi-cloud resources
For many organizations, the first step in strengthening their security posture is to configure cloud resources in a secure manner that minimizes exposure to risks and reduces the overall attack surface. This step can also play an important role in meeting internal and external compliance requirements.
Microsoft Defender for Cloud gives you deep visibility into the security state of your cloud environments—including Azure, Amazon Web Services (AWS), and Google Cloud Platform (GCP). Secure Score gives you an assessment of your current state and provides prioritized recommendations for actions you can take to improve your overall security posture and remediate common misconfiguration issues, such as failing to enable encryption for data at rest; updates that haven’t been installed; or lack of network security layers, such as firewalls, implementing role-based access control, or improving container configurations.
Microsoft Defender for Cloud continuously monitors your environment and discovers new resources and workloads. When a new resource is discovered, it is assessed against security best practices, and anomalies are flagged. Microsoft Defender for Cloud then recommends fixes to better protect your resources and services.
With Mazzy Technologies, Microsoft and ServiceNow automation with bring your organization:

Cloud-native protection with Microsoft’s leading threat protection technologies and shared intelligence
Microsoft Defender for Cloud provides advanced protection for servers, containers, and other cloud workloads. Its built-in behavioral analytics and machine learning help you identify vulnerabilities and advanced persistent threats, and you can monitor your cloud resources for known attack patterns and post-breach activity. With prioritized security alerts and incidents, Microsoft Defender for Cloud can help you detect and protect against new and emerging threats.
Microsoft Defender for Cloud is designed to protect your multi-cloud state,
including Azure-native services, workload protection for Amazon Elastic Kubernetes Service and Amazon Elastic Container Service, along with Google Kubernetes Engine Standard clusters and Google Compute Engine virtual machines (VMs).
Take advantage of broad workload coverage
Microsoft Defender for Cloud, backed by the power of leading threat intelligence capabilities, provides broad coverage of your cloud workloads, such as:
Microsoft Defender for Cloud integrates with Microsoft Purview, a unified data governance solution that helps you manage your multi-cloud and SaaS data. The integration enables you to use Microsoft Defender for Cloud to better discover, classify, track, and secure sensitive information across your workloads and improve your security posture through better prioritization and recommendations. Just as Microsoft Defender for Cloud gives you a bird’s-eye view of your cloud environments, Azure Purview extends that view into your data and data storage systems, broadening your ability to prioritize actions based on the sensitivity of your data.

Enable streamlined, secure, and controlled access to data and services in the cloud
Another critical element of a comprehensive cloud security strategy is controlling and managing user access to apps, data, and services. According to Forrester Consulting, the average enterprise has more than 1,000 cloud apps and services, half of which go unmonitored by IT.
In addition to single sign-on, conditional access in Azure AD enables you to enforce fine-tuned adaptive access controls, such as requiring multifactor authentication, based on user context, device, location, and session risk information. Move beyond simple access/block decisions and tailor decisions based on risk level, such as allowing, blocking, or limiting access, or requiring additional authentication methods, such as a one-time passcode or a biometric input. Augment this by ensuring that only healthy, trusted devices are allowed access to your corporate resources by checking the device health and security posture of registered devices.
Ensure least-privilege access for all identities in your multi-cloud environment
IT administrators are no longer the only users who have permissions to access critical cloud apps, data, and services. Developers; third-party contractors; and workload identities, such as bots, API keys, and VMs, also have access to your cloud resources. Today, more than 40,000 permissions can be granted to identities across the major cloud platforms, and nearly 50% of these permissions can be classified as high risk, with the ability to cause catastrophic damage if used improperly. To add to this, more than 90% of identities are using less than 5% of their granted permissions to perform their job function.6 The result is a significant—and highly exploitable—permissions gap.
Microsoft Entra Permissions Management is a cloud infrastructure entitlement management solution that provides comprehensive visibility into permissions assigned to all entities—users and workloads—actions, and resources across cloud infrastructures. It detects, right-sizes, and monitors unused and excessive permissions and enables Zero Trust security through least-privilege access in Azure, AWS, and GCP.
Control the access and use of SaaS apps
Microsoft Defender for Cloud Apps, Microsoft’s leading cloud access security broker, gives you visibility into apps used in your environment and the ways workers are using and interacting with these apps. This helps you identify unsanctioned apps, assess their compliance risk, and make informed decisions about allowing ongoing use. Microsoft Defender for Cloud Apps continues to expand its support for SaaS apps and now covers more than 26,000 apps.
With Microsoft Defender for Cloud Apps, you can:

Build, deploy, and operate secure code and apps in the cloud
Microsoft Defender for Cloud Apps, and other tools to better secure Microsoft and third-party apps, but what about the apps and code that your organization develops, deploys, and operates? Securing your code and apps is just as important as securing other aspects of your cloud environment. This can be accomplished by integrating security into the entire app-development and operations lifecycle—an approach commonly called DevSecOps.
In a world where 83% of code vulnerabilities are caused by development errors, an integrated DevSecOps approach helps developers integrate security into every step of the lifecycle. GitHub Advanced Security is a developer-first, community-driven service that makes it easier to secure your apps. It provides:
• Dependency scanning: The service continuously assesses the risk levels of dependencies the code uses.
• Code scanning: As code is generated, GitHub Advanced Security scans it and displays the results for easy remediation.
• Secret scanning: The service scans the code for hard-coded credentials or tokens.
Integrate security into entire DevOps lifecycle
Take advantage of the integration between GitHub and Microsoft
Defender for Cloud to better connect DevOps and SecOps
As powerful as GitHub is, it’s even better when used along with Microsoft Defender for Cloud. Together, these solutions provide the tools and visibility to help developers kickstart DevSecOps practices. For example, the results from container scans appear in Microsoft Defender for Cloud, giving security teams a better understanding of the source of vulnerable container images and the repositories they came from. Developers can scan for common vulnerabilities before pushing images to a container registry or deploying them to a containerized web app or Kubernetes cluster.
Copyright © 2024 Mazzy Technologies - All Rights Reserved.
We use cookies to analyze website traffic and optimize your website experience. By accepting our use of cookies, your data will be aggregated with all other user data.